Consumer Packaged Goods (CPG) production sites benefit from connecting plant floor packaging equipment to their local area network to deliver vital live data, system status and send notifications. Unfortunately for many, this task is daunting and complicated due to IT security concerns, policies and fortified firewalls. The risk of allowing “outsiders” connect into the company’s IT system using conventional network connections can simply outweigh the reward. Are there any alternatives?
This is where Machine-to-Machine (M2M) network technology comes in. M2M technology involves machines and devices communicating data to each other over a wireless broadband service using a CDMA or GSM mobile access network. M2M networks allow packaging equipment devices to share data without the need to infiltrate local or remote IT network sites. This means the need to connect through your firewalls or run application software on your company’s servers is unnecessary.
With M2M connections expected to reach 1 billion users by 2020, security is the key to future-proofing the M2M global community. Mobile carriers are implementing innovative and the best commercially available methods to minimize the security risk that make this network system reliable and sustainable. To provide a secure mobile service like CDMA, there must be two types of access networks (AN) for the remote device to connect to the Internet of Things (IoT). The access network maintains the communications link between the mobile station and the core network. Between these two access networks, Roundtrip Time (RTT) and Evolution-Data Optimized (EV-DO), a combination of 27 requests, assignments and responses are processed using CAVE based authentication that deploys Authentication Key (A-key) and Shared Secret Data (SSD) encryption. In layman’s terms, breaking the security of M2M is very difficult, there is no denial of service risk, and with no need to connect your server to the equipment, there is no threat of introducing visitors through your IT network system.
 Redimark recently launched a small character inkjet date coder for CPG product manufacturers that utilizes M2M networks for Internet of Things (IoT) data delivery. An inkjet date coder’s controller is, in general terms, a computer with a real time clock. It has the ability to capture what product was date coded, how much and when. It can even record some environmental elements such as what operators are working the production line. We believe that making the inkjet date coder a member of the IoT is important because historical production data and current operation status is meaningful for your business that delivers efficiencies in many areas.
Redimark recently launched a small character inkjet date coder for CPG product manufacturers that utilizes M2M networks for Internet of Things (IoT) data delivery. An inkjet date coder’s controller is, in general terms, a computer with a real time clock. It has the ability to capture what product was date coded, how much and when. It can even record some environmental elements such as what operators are working the production line. We believe that making the inkjet date coder a member of the IoT is important because historical production data and current operation status is meaningful for your business that delivers efficiencies in many areas.
We believe that making the inkjet date coder a member of the IoT is important because historical production data and current operation status is meaningful for your business that delivers efficiencies in many areas.
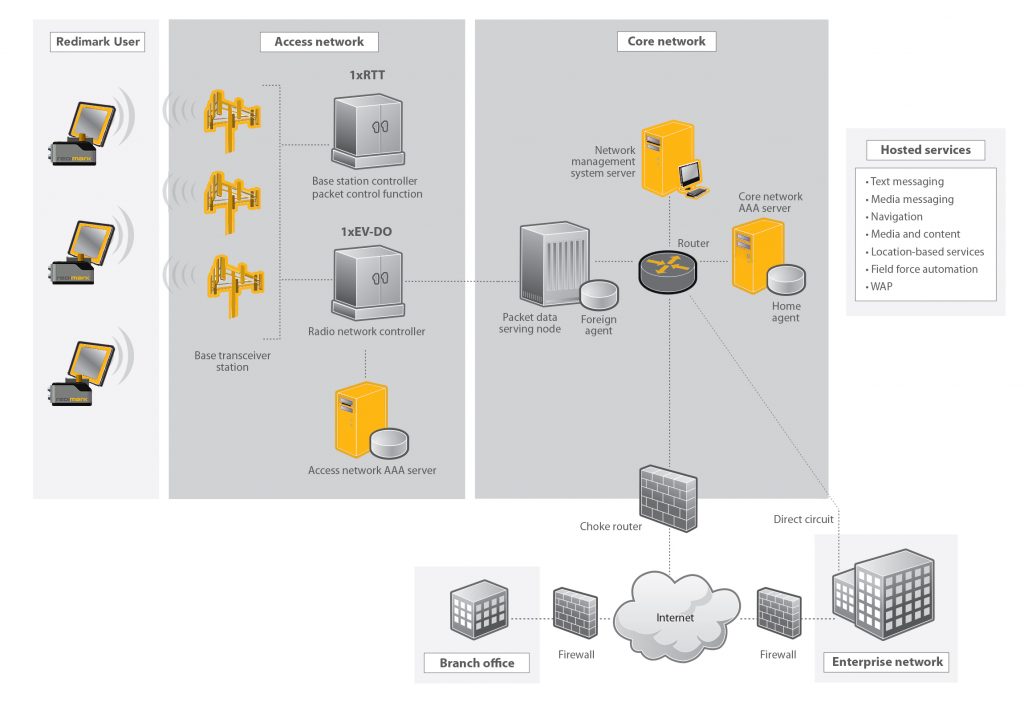 Above: A simplified M2M CDMA2000 1x data network showing 1xRTT and 1xEV-DO data structures
Above: A simplified M2M CDMA2000 1x data network showing 1xRTT and 1xEV-DO data structures
Benefits of the Redimark TC12 Thermal Inkjet Date Coder device connected to a M2M network:
- Secure data connectivity between the Redimark device and its services.
- Continuous monitoring and real-time information increases production efficiency.
- Easy data integration for cloud based software as a service (SaaS) functions.
- Authorized users can view data anywhere around the globe using a web portal.
- No risk of losing connection with the Redimark device due to a change in the device’s IP address. The provider’s access network Mobile IP service manages the static IP address of the Redimark device.
- The Redimark device continues to perform during interruptive network outages.
- here is no IT hardware to maintain or upgrade.
When the team at Redimark designed its latest inkjet date coder, they carefully considered all options to offer a flexible and secure data delivery method. Redimark benchmarked other industries that relied on M2M security, such as manufacturers of vending, ATM machines and medical devices. This is just an example of devices that use M2M for data exchange to process credit card data or patient medical information. These device manufacturers have trusted M2M to meet their strict internal and governmental security standards. Beyond the M2M hardware and software security layers deployed, Redimark has added a layer of data security known as the Transport Layer Security (TLS). TLS is a cryptographic protocol that might sound strange, however, it is all well known to those that use online banking or PayPal. You might recognize the URL header ‘https’ in the address bar of your web browser. TLS is a layer of security trusted by the global Internet community that makes Redimark products and software more secure and reliable.
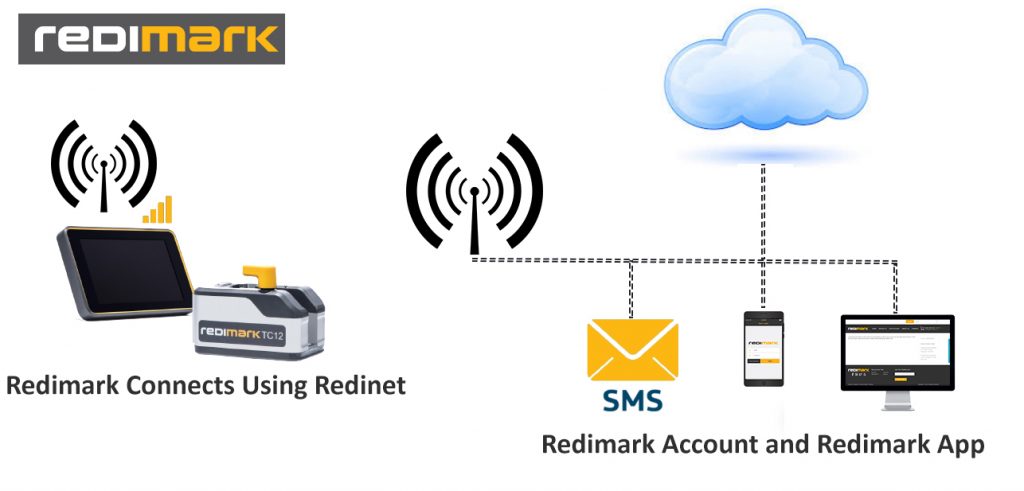
Above: Redimark and the M2M IoT data network topology
Redimark is all about delivering a simple user experience. To keep that promise, the inkjet date coder is shipped preloaded with the M2M hardware and therefore, no M2M setup is required. This makes it very easy to install and it will only take minutes before you can operate your Redimark TC12 Thermal Inkjet Date Coder. Not only does Redimark aim to deliver a user experience that is simple, reliable and intuitive, Redimark wants your experience to be secure and one that can be trusted. To learn more about the Redimark TC12 Inkjet Date Coder visit redimark.com.
About Dean Hornsby
As Redimark’s Brand Evangelist, Dean is a passionate guy. Passionate about sharing his deep knowledge about packaging and automation, passionate about exceptional customer satisfaction, and a bit nutty about perfectly printed date codes. Nothing makes him happier than matching Redimark’s solutions with your business’s coding and marking needs (well, that and a good craft beer). In his more than 25 years in the Fast-Moving Consumer Goods (FMCG) industry, Dean has done and seen it all; from engineering to plant automation to vision and coding systems. Have a question for Dean? He’d love to chat.